08
2025
-
09
FD-ACN1B TCP/IP Web 1 Door 2 ways WEB Server Access Controller
In the realm of modern access control systems, the FD-ACN2B TCP/IP Web 1 Door 2 ways WEB Server Access Controller stands out as a reliable and feature-rich device.
Author:
FD-ACN1B TCP/IP Web 1 Door 2 ways WEB Server Access Controller:
A Comprehensive Introduction
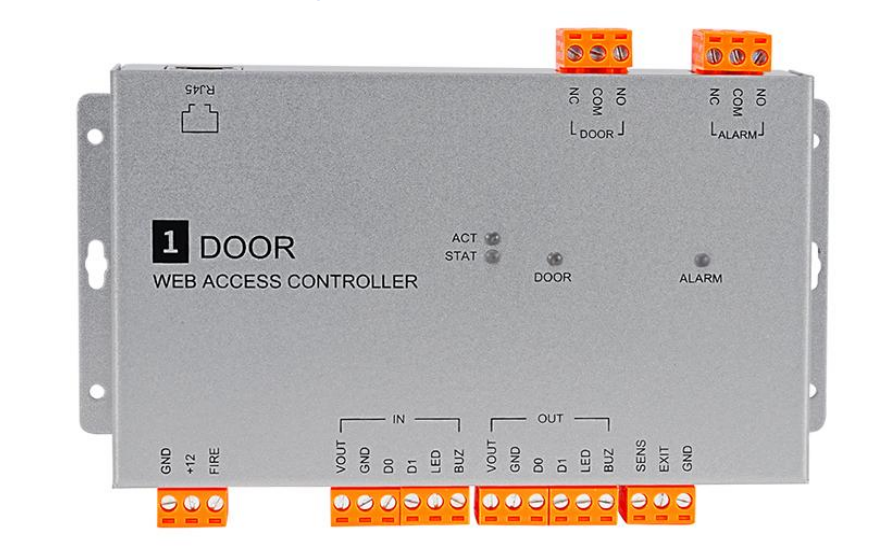
In the realm of modern access control systems, the FD-ACN2B TCP/IP Web 1 Door 2 ways WEB Server Access Controller stands out as a reliable and feature-rich device. This controller is designed to manage access to a single door with bi-directional control, making it suitable for a wide range of applications, from small offices to residential buildings.
1. Basic Specifications
User Capacity: With the ability to accommodate up to 100,000 users, the FD-ACN2B is well-suited for large-scale deployments. This high user capacity ensures that even in busy environments, the controller can handle the access needs of a substantial number of individuals.
Event Record Capacity: It can store up to 100,000 event records. This comprehensive logging feature allows for detailed monitoring and auditing of access events, which is crucial for security and compliance purposes.
Processor: Equipped with a 32-bit processor, the controller offers efficient and fast processing of access requests. This ensures smooth operation, even during peak usage times.
Memory (RAM): Although the exact capacity of the 32-bit RAM is not specified, it is optimized to support the controller's functions, enabling quick access to user data and event records.
Power Requirement: The controller operates on DC 12V, 1A power supply. This standard power requirement makes it easy to integrate into existing power systems.
Power Consumption: Without external devices, the power consumption is 500mA, indicating its energy-efficient design.
2. Interface and Connection
TCP/IP Interface: The RJ45 TCP/IP interface supports a WEB Server, enabling seamless connectivity to a network. This allows for remote management and monitoring of the access control system. While the specific TCP/IP standards such as HTTP/HTTPS support are not explicitly stated, it is expected to support common web-related protocols for easy access and configuration.
Reader Input: There are 2 reader inputs that support Wiegand 26/34-bit protocols, which can be customized. This flexibility allows for the use of a wide range of card readers, enhancing the system's compatibility.
Other Connections: It has 1 connection for an exit button, 1 for an EM lock, 1 for a sensor, 1 for a fire alarm input, and 1 event-triggered relay output. These connections enable the controller to integrate with various other security and access control devices, creating a comprehensive security solution.
3. Physical Parameters
Size: Measuring 172.5 × 115.5 × 27.5 mm, the controller is compact and can be easily installed in various locations. Its small footprint makes it suitable for both new installations and retrofits.
Weight: Weighing only 460g, it is lightweight, further facilitating installation and transportation.
4. Function and Management
Management of Doors: The FD-ACN1B manages 1 door with bi-directional control, providing secure access in both directions.
Communication Mode: It uses the Wiegand protocol for communication with connected devices, ensuring reliable data transfer.
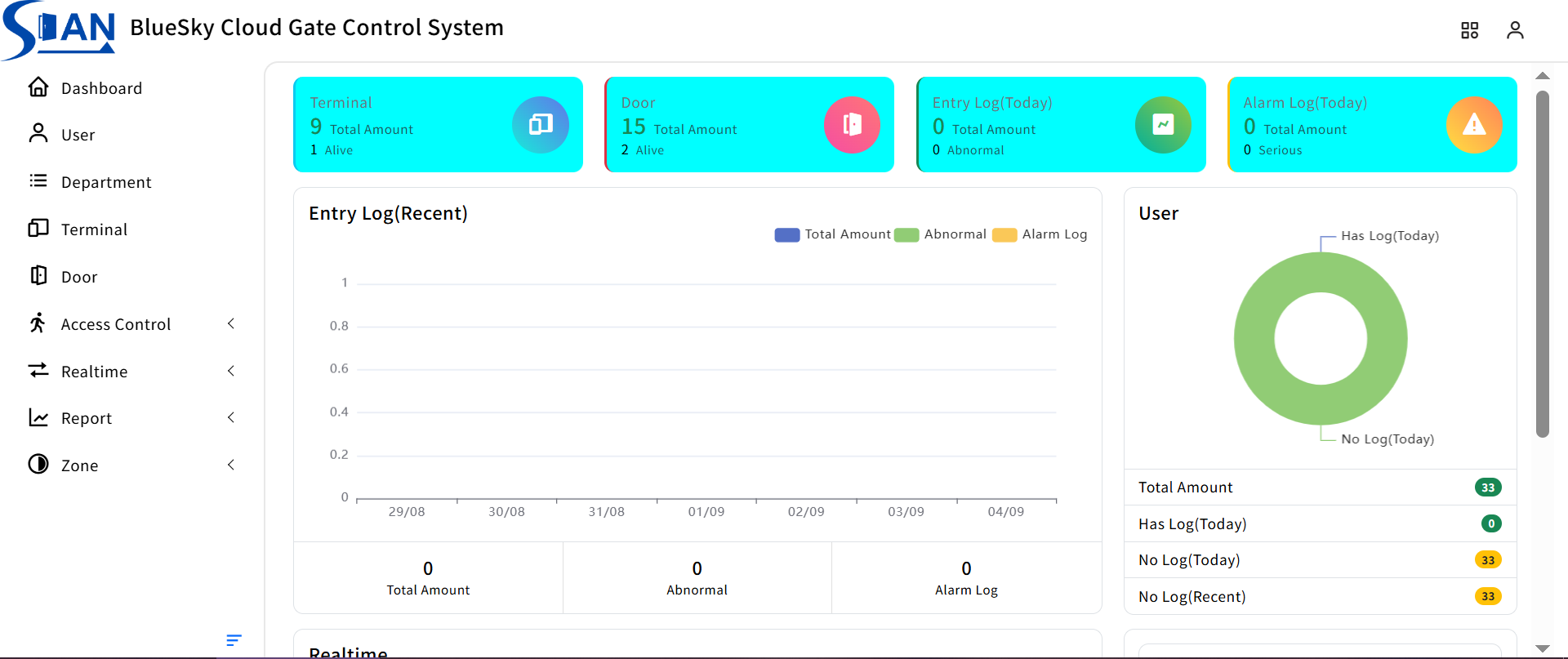
5. Cloud-based Software Integration
To fully utilize the capabilities of the FD-ACN1B, it is designed to work in tandem with a cloud-based software solution. The device at the front-end, the FD-ACN1B controller, collects data from card readers, sensors, and other connected devices. This data includes access requests, door status, and alarm events.
The cloud-based software, on the other hand, provides a user-friendly interface for viewing and managing this data. Administrators can log in to the software from any location with internet access to monitor real-time access events, review historical records, manage user permissions, and configure system settings. For example, they can add or remove users, set access schedules, and receive alerts in case of any security-related events.
The software also offers features such as reporting and analytics. It can generate reports on access patterns, peak usage times, and any unauthorized access attempts. This data can be used to optimize security measures and improve overall access control management.
Take the first step to streamline your transactions—contact us today!
Email: info@forddok.com
Phone: +86 13410323028
Visit https://www.forddok.com to learn more and request a free quote.
News
2025-10-03
2025-04-01
2025-03-27









